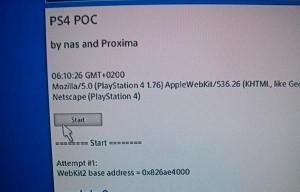
All throughout PlayStation history hackers have been hard at work trying to find new ways of breaking the system software of Sony’s gaming consoles. A recent breakthrough in this sense was achieved by two freelance developers, nas and Proxima, who have found a method to implement their Webkit exploit originally designed for the PS Vita into the PS4 firmware 1.76. In spite of the fact that this is the same webkit exploit, it was developed in parallel to that of PS Vita, and not based on it, Proxima explained. The two hackers provided a proof of concept code entailing several samples that include a module dumper and a series of tools for creating advanced ROP code, published by Wololo.
It seems that the code per se looks genuine and might create some damage in the hands of other developers who are trying to find new ways of hacking the PS4 firmware. The webkit exploit itself will not be of great help to the mainstream user, except for the fact that it will indicate if their PS4 is breakable. Hacking duo, nas and Proxima have speculated on a vulnerability in the console’s Web browser running on firmware 1.76, and managed to break it. This hack is a massive road opener for PS4 enthusiasts who now have a back door into the system, and will be able to further explore its functionality and vulnerabilities. Apparently, there are two versions of the Webkit: a 32 bit version and a 64 bit.
Proxima shared the following: “The 64bit version is a bit different. It is the same heap corruption via the sort() bug, but from there its different. On 32bit you can set the Uint32Array to 0x40000000 size and access any memory. On 64bit, you have to carefully change the base address since the 0x40000000 trick doesn’t work for a 64bit address space.” Sony’s “Masamune” PS4 2.0 update is scheduled to arrive this week, so if you plan on using the firmware 1.76 exploit, it would probably be a good idea not to update to the new firmware. You can download the PS4 firmware 1.76 Webkit exploit here.
 Load the Game Video Games, Reviews, Game News, Game Reviews & Game Video Trailers
Load the Game Video Games, Reviews, Game News, Game Reviews & Game Video Trailers