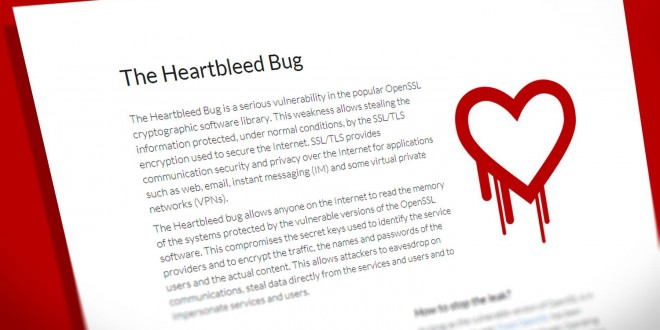
The Heartbleed bug that was published this spring was not fixed yet and several vulnerabilities have been discovered today affecting all versions of the Open SSL. The Open SSL 0.9.8, 1.0.0, 1.0.1 and 1.0.2 have been affected one more time by seven vulnerabilities. The man-in-the-middle attack, one of the bugs referred to a CCS injection has been dubbed as “serious”. Also, the 1.0.2 beta release is not yet updated and currently vulnerable. The team recommends those who are running one of the affected versions to upgrade as soon as possible. The vulnerabilities “allow malicious intermediate nodes to intercept encrypted data and decrypt them while forcing SSL clients to use weak keys which are exposed to the malicious nodes”, as explained by the team. The heartbleed bug was found by Masashi Kikuchi of Lepidum while studying safe TLS implementations. Hopefully, with the whole team’s help, the Heartbleed bug will stop being a concern in the next few weeks.
In order to stop the leak, a system update is absolutely necessary and software updates can be applied for each vendor. Solutions can be found for Ubuntu, Debian, FreeBSD, CentOS, Red Hat 5, Red Hat 6 and Amazon Linux AMI. For those who are wondering if the private keys and certificates need to be recreated, the answer is no. In case you have transferred the private keys via paths protected by SSL/TLS, the keys could be sniffed, however. In that case, regenerating the keys and certificates could be a good idea.
Massashi Kikuchi explained that the main reason why the heartbleed bug has not been found for over 16 years is simple. The code reviews were not sufficient and the reviewers were not experienced enough. So everything is a matter of human resources and experience in the end. Also, the Open SSL code should have been verified and the problem could have been detected in time.
 Load the Game Video Games, Reviews, Game News, Game Reviews & Game Video Trailers
Load the Game Video Games, Reviews, Game News, Game Reviews & Game Video Trailers